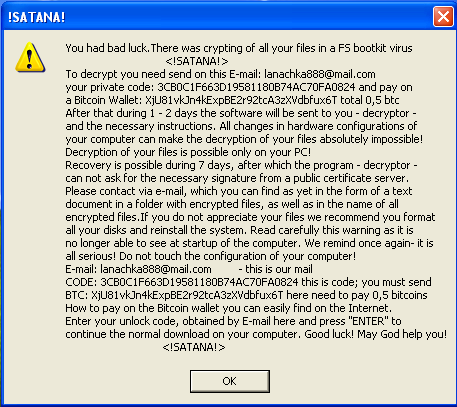
Unpacking Satana Ransomware
Satana is a very recent ransomware that, like Petya, will encrypt your files and infect the Master Boot Record. Since the payload has already been reversed and analyzed, I will only focus on the unpacking part.
Sample
The dropper I will be using can be downloaded here if you have a Malwr account.
MD5 46bfd4f1d581d7c0121d2b19a005d3df
SHA1 5b063298bbd1670b4d39e1baef67f854b8dcba9d
SHA256 683a09da219918258c58a7f61f7dc4161a3a7a377cf82a31b840baabfb9a4a96Anti-Debug tricks
Some of the anti-debug techniques I found traces of in the dropper :
ntdll!ZwQueryInformationProcess()kernel32!SetUnhandledExceptionFilter()kernel32!OutputDebugStringA()kernel32!GetLocalTime()- ...
These tricks are well known and common, you can try and bypass them using this article by Symantec or by installing the ScyllaHide plugin for OllyDbg (or equivalent).
Extracting the payload
We can find multiple references to RtlXXX() functions in the code : the dropper uses the RtlDecompressBuffer() method to decompress the payload in memory and then drops it in the %TEMP% folder under a random name.
Let's put a breakpoint on RtlDecompressBuffer() (Ctrl+G -> ntdll.RtlDecompressBuffer -> Follow label -> Breakpoint on first instruction).
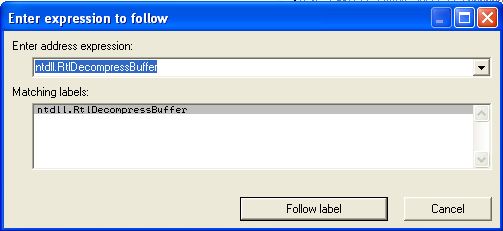
Here is the prototype of this function :
NTSTATUS RtlDecompressBuffer(
_In_ USHORT CompressionFormat,
_Out_ PUCHAR UncompressedBuffer,
_In_ ULONG UncompressedBufferSize,
_In_ PUCHAR CompressedBuffer,
_In_ ULONG CompressedBufferSize,
_Out_ PULONG FinalUncompressedSize
);We are interested in the second and third parameter.
When OllyDbg hits the breakpoint, look at the call stack :
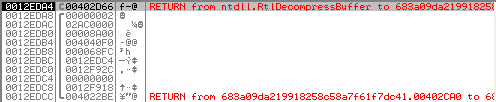
At 0x0012EDAC, we can read the pointer to the buffer in which the payload will be written : 0x02AC0000 and at 0x0012EDB0, the size of the buffer : 0x8A00 = 35328 bytes. Right click on 0x02AC0000 in the call stack window and click on "Follow in dump". Then, in the dump window, right click on the first byte and put a memory breakpoint on Read and Write access so we can monitor it.
We can resume execution and we hit the memory breakpoint when RtlDecompressBuffer() starts writing data. You can see it being written byte by byte. You can then press Ctrl+F9 until you get back to the dropper module. You can see the buffer has now been filled. It doesn't look like it contains a Portable Executable file yet since it's encrypted.
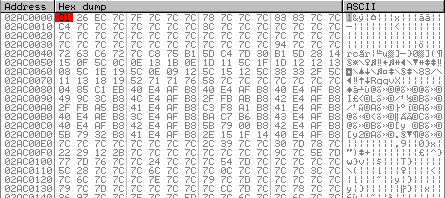
Debugging step by step, we end up in the decryption loop that starts at 0x00402B50 and ends at 0x00402BC7. Put a breakpoint at this offset and resume execution.
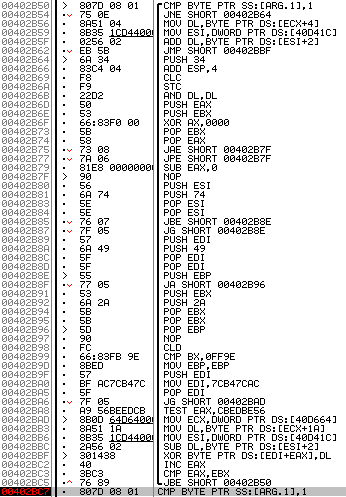
We can now see the decrypted payload in the dump window. You can extract it by selecting 35328 bytes and clicking on "Open in a separate dump window". Then, to save the payload as a file, click on "Backup" and "Save data to file" in the context menu.
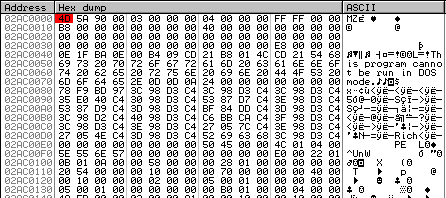
Here are the hashes of the payload :
MD5 a5444dd6ee8773915096c31bd882e247
SHA1 88265756945984ebd5fe58827c39ca1f1a2bf487
SHA256 ea2c169529e782994be5296c81ff4668dba2b77a805bd057b53e5952c65aaf72You can see the payload sandbox analysis on  Malwr and
Malwr and  VirusTotal.
VirusTotal.
If you are interested in the payload analysis, you can read this article by @hasherezade from MalwareBytes.